Publications
2025
-
-
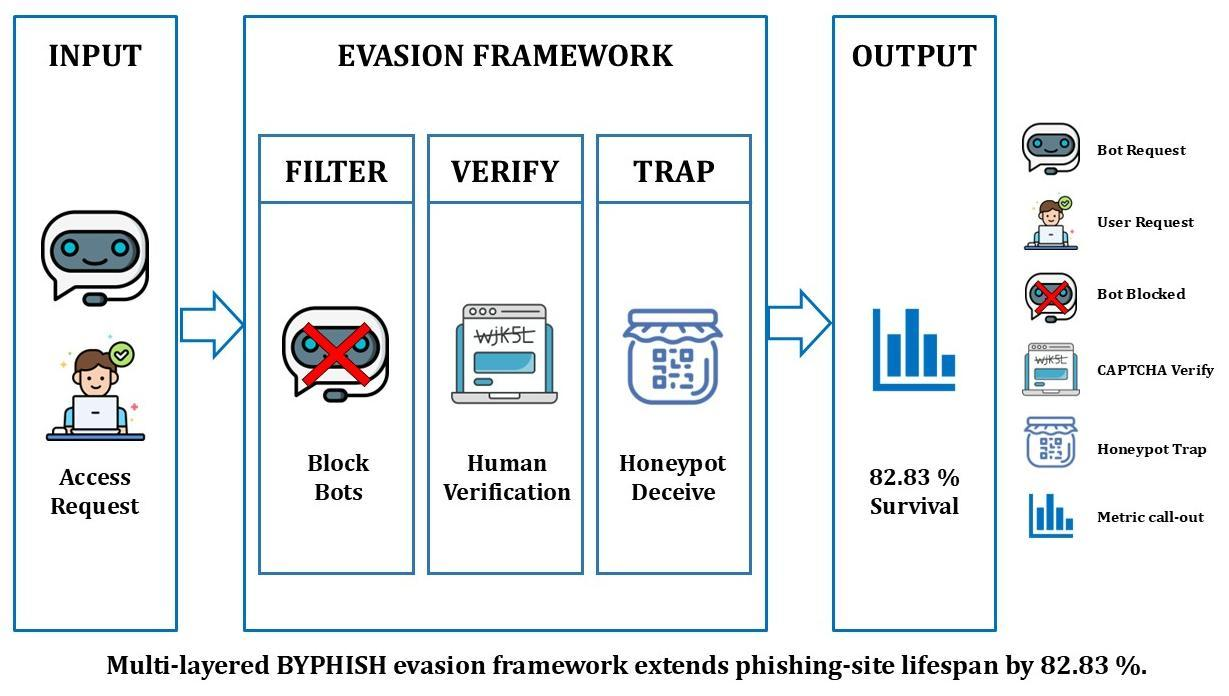
Decoding Phishing Evasion: Analyzing Attacker Strategies to Circumvent Detection Systems
A. GHAFOOR, M.A. SHAH, M. AL-NAEEM, C. MAPLE
IEEE Access(2025)
ABSTRACT BIB
Phishing remains a critical security threat, involving the creation of fraudulent websites to capture sensitive information. Despite existing detection systems, sophisticated attackers have developed advanced evasion techniques that undermine these defenses. This paper highlights the significant challenge of these novel methods, focusing on how attackers manage to prolong the operational lifespan of phishing sites. Our research investigates how attackers circumvent traditional security layers by employing a combination of target filtering mechanisms, bot detection evasion, blacklisting avoidance, and honeypots. Our experimental findings indicate that these evasion strategies can achieve an effectiveness rate of 80% to 85% in extending the viability of phishing sites. We have empirically demonstrated the exposure of current systems to these attacks, revealing specific vulnerabilities and exploitation points. These results underscore the urgent need for enhanced detection frameworks that address the layered and adaptive nature of modern phishing tactics. Our work highlights a critical gap in current security measures and poses a challenge to solution providers: there is a pressing need for novel mitigations to safeguard users against these sophisticated phishing threats.
2024
-

-
Discover and Automate New Adversarial Attack Paths to Reduce Threat Risks for The Security of Organizations
Ghafoor, Azhar; Shah, Munam Ali; Zaka, Bilal; and Nawaz, Muhammad
Journal Paper in IPSI Transactions on Internet Research(2024)
ABSTRACT BIB
Phishing remains a pervasive cybersecurity threat, leveraging social engineering and technological deception to obtain sensitive information and credentials. This research explores novel attack paths employed by sophisticated adversaries, focusing on the identification and analysis of emerging tactics to enhance understanding and awareness of evolving phishing threats. The study uncovers various attack vectors, including the impersonation of reputable entities and the exploitation of legitimate platforms for malicious purposes. Notably, it highlights the increasing prevalence of documentbased and social media-based phishing campaigns, underscoring the adaptability of attackers in exploiting diverse channels to deceive users. Furthermore, the research evaluates the effectiveness of current countermeasures and proposes actionable strategies to mitigate phishing risks for organizations. Recommendations include strengthening email protection measures, implementing robust web filtering systems, and conducting simulated phishing campaigns to enhance employee awareness. By providing insights into emerging attack paths and practical recommendations, this research contributes to the ongoing efforts to combat phishing threats and strengthen cybersecurity resilience. The findings underscore the critical importance of proactive measures and continuous vigilance in safeguarding against evolving cyber threats in today's dynamic digital landscape.
2021
-
-
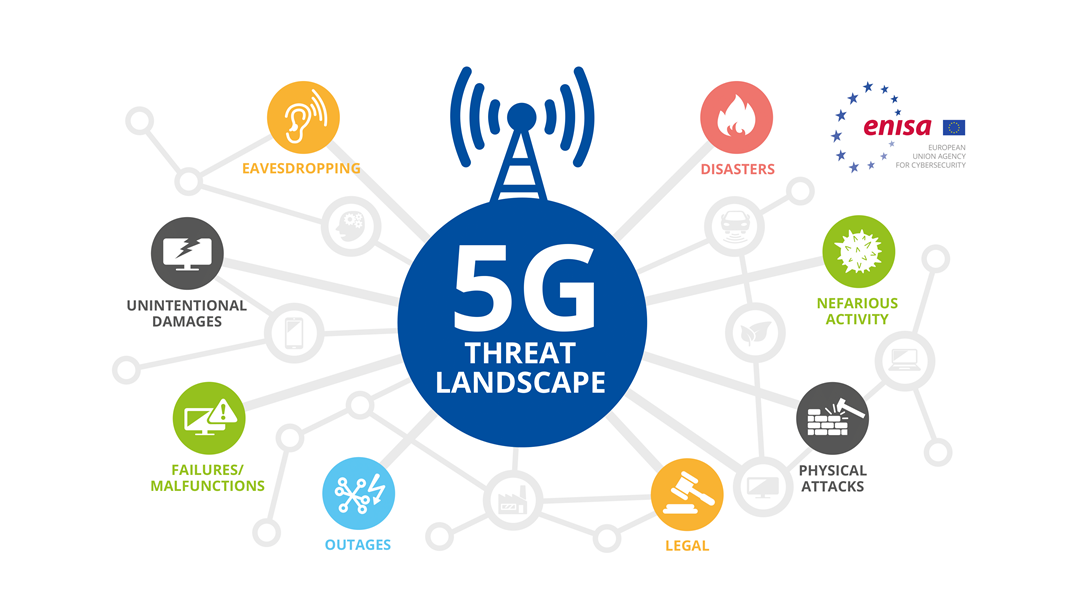
5G Security Threats Affecting Digital Economy And Their Countermeasures
Ghafoor, A., Shah, M. A., Mushtaq, M., Iftikhar, M.
Conference Paper in IET Digital Library(2021)
ABSTRACT BIB
The fifth-generation (5G) network is set to provide extensive connectivity for sharing information and data with low latency rates, increased bandwidth, and a broader frequency spectrum, ultimately boosting speed. Securing Massive Internet of Things (IoT) devices is paramount to ensure secure communication among various devices. While 5G wireless communication introduces new services and frameworks, it also magnifies security concerns. Additionally, it poses significant challenges to user privacy. This report offers a comprehensive overview of the threats and challenges inherent in 5G networks and presents potential solutions. Furthermore, 5G is leveraged to enhance communication security and provide essential building blocks for physical layer security.
-
-
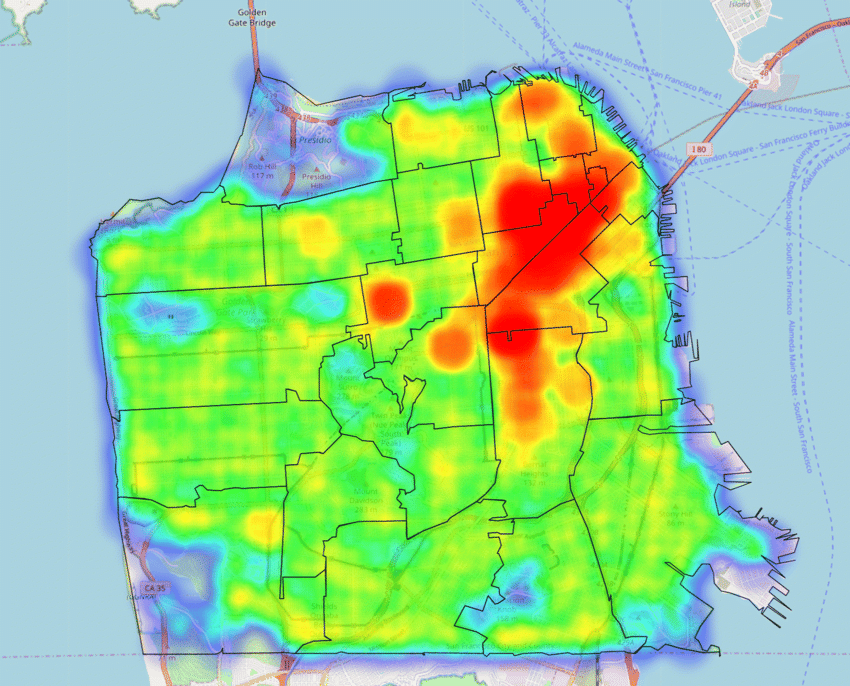
Forecasting the Trends and Patterns of Crime in San Francisco using Machine Learning Model
Rasool, S., Ghafoor, A., Fareed, Z.
Journal Paper in INTERNATIONAL JOURNAL OF SCIENTIFIC & ENGINEERING RESEARCH, VOLUME 12, ISSUE 6, JUNE-2021(2021)
ABSTRACT BIB
The Crime Prediction Method is a systemic approach to preventing the detection and review of past crime data patterns and trends and uses it for future crime forecasting. This system is designed to predict the type of crime in a given region that is highly likely to occur and can view areas susceptible to crime. Crime analyzers are helping law enforcement officers to solve crimes with the growing advent of computerized systems. Using machine learning methods, we can derive information from past crime data that is unknown and useful before and can predict future crimes. Here we are working to build a machine learning procedure between computer science and criminal justice, so that crimes can be resolved faster. Instead of focusing on the causes of crime, such as crime, political hostility, etc., we concentrate mostly on the crime factors of every day.
-

-
The Internet of Medical Things (IoMT): Security Threats and Issues Affecting the Digital Economy
Mushtaq, M., Shah, M. A., and Ghafoor, A.
Conference Paper in IET Digital Library(2021)
ABSTRACT BIB
In the healthcare industry, we cannot deny, contradict, or oppose the importance of the Internet of Medical Things (IoMT). The ultimate purpose of the IoMT system is to gather and transmit health information, including ECG readings, weight measurements, blood pressure data, and sugar levels. This data may be shared with authorized individuals, such as physicians, participating health companies, insurance providers, or external contractors, regardless of their time, location, or device. However, the situation is not as straightforward because IoMT faces various emerging cyberattacks and threats. New malware attacks targeting IoMT are created and launched daily because attackers recognize the immense value of this market, worth billions. The purpose of this paper is to introduce you to some of the well-known attacks targeting IoT, including denial of service, router attacks, sensor attacks, replay attacks, fingerprinting, time-based spoofing, and recent malware attacks like Miari, Emoted, Gamut, and NE curs, as well as ransomware in IoMT.
* Joint first author.